By definition, an information system is "a collection of hardware, software, data, people, and procedures that work together to produce quality information." As we all know, hardware, software, data, people, and procedures often change. To make this change effective you must follow the five phases of the system development life cycle. The five phases that I will breakdown and discuss in detail are (1)planning, (2)analysis, (3)design, (4)implementation and (5)operation, support and security.
The first phase is in the SDLC is planning. The planning phase starts as soon as a request for a change is requested. During this phase there are four activities that you must follow. (1) review and approve the project, (2) put the requests in order of importance, (3) divide up the resources and (4) form a project team.
After the planning phase has been approved you will move into the analysis phase. In this phase there are two major activities that you and the team must follow. (1) investigate the problem and (2) perform the analysis on the problem. The first step will determine what the problem is and how to improve it. You may find that the problem is not worth pursuing during this step. If it is a problem that needs to be addressed then you will perform the analysis. In the analysis phase you want to study how the current system works and find out how the users want it to work. After you have collected this information then you will propose a solution.
The third step in the SDLC is the design. You must collect all the hardware and software and develop all the details of the new system. Once the requirements for the new system has been ironed out, collect proposals from vendors. The lowest bid is not always the best bid. You need to find a vendor that can deliver exactly what you need. Always get a list of references from the vendor and talk to current users.
Next you will move into the implementation phase. During this phase you will develop the system, install and test the new system, train the users and finally, convert to the new system. One of the top reasons a project fails is poor training. Training can be done one on one or in a classroom setting. Training on a new system should always be hands on training. If the training is not done correctly, the new system will fail.
The final step is the operation, support and security phase. In short you can call this the maintenance phase. You will monitor the systems performance and fix errors as they come up. If you are the system designer then you must meet with users and get their feedback. The users of the system can tell you where there might be an error or where a system enhancement is needed. Below is a chart that will help remind you of all five steps. Do not skip any of these steps. Although these steps can be time consuming, it will lead you to a successful system roll-out.
Image Created by Dawn Holloway
Sources
Discovering Computers 2010 Living in a Digital World
Wikipedia
Dawn's ISM3004 Blog
Welcome Student Bloggers
I hope that you all find my blog to be of use in our time together in ISM3004
Sunday, April 17, 2011
Sunday, April 10, 2011
Secure Email Project
This secure e-mail project has been very interesting. Before this assignment, I never realized how important that it is to send emails that have been digitally signed and/encrypted. It is a sure way to ensure that hackers cannot access viable information.
Below is a link of an article that discusses the hacking of Sarah Palin's email during the Presidential race. Because she was using her personal email, and not the secure email of her state, her information had been compromised. No one should have their email compromised, but being in the very public eye, left her susceptible to would-be hackers. The article also discusses that even if she didn't know better, the political big-wigs of McCain's campaign should have ensured the utmost security. Her personal information was all over the internet, which posted possible damage to the McCain campaign.
Saturday, March 26, 2011
Database Project
This was a pretty difficult project. I had a hard time relating the video lesson material to the actual practical application. A lot of it was trial and error, but in the end it did work. I took a Microsoft Office class when I got my AA at FSCJ and the material in that class was pretty straight forward. There was a small section on access, but it was an online class and all of the instructions were printed. I did get more familiar with a lot of the different aspects of access, i.e. reports, queries and forms. So I do feel confident that in the future were I to need to create a database, that I would be able to figure most of it out.
As far as enhancing the functionality of an access database, I think the availability of an access "wizard" would be very helpful. The individual "wizards" helped tremendously, but having one "wizard" that was able to take you from the beginning to the end would be great. There would be no guessing as to what type of information that you needed to create, i.e. report, or form, because the wizard would be able to do that for you.
As far as enhancing the functionality of an access database, I think the availability of an access "wizard" would be very helpful. The individual "wizards" helped tremendously, but having one "wizard" that was able to take you from the beginning to the end would be great. There would be no guessing as to what type of information that you needed to create, i.e. report, or form, because the wizard would be able to do that for you.
Thursday, March 24, 2011
Tutorial 3: Effective Passwords
Many of us visit websites or create private accounts on the internet everyday. We also have private information on our computers that would be detrimental to us if someone were to hack into that account and use that information. The alarming part of this is that many of us use passwords that can be easily discovered. I will teach you how to create an effective password. I will help you create passwords that can be easily remembered by you, but hard for a hacker to figure out.
Strong passwords are usually 6-16 characters long. You will want to have at least one capital letter, one numeric value and one symbol in the password. The longer the password , the longer it will take for someone to figure out. An example of this would be: Jerremy93$. This could be your first name, the year you were born and any symbol that you might want to use. This ten digit code could take a person millions of years to discover. This is due to several different combinations that could be used even if someone knew my name and date of birth.
When you visit a website and set up an account, the server will ask you for personal information in case you forget your password. An example most commonly used is mother's maiden name. Since the input is case sensitive, you might want to be creative when entering the information. An example might be: hoLLoway. If a person knew my mother's maiden name, they would still have a hard time figuring out how it was entered.
Once you have created a password, the next step will be to change it frequently. This might be every six months or so. When changing your password, do not make the mistake of just changing one value such as Jerremy94$. If someone knows your password already, this would make it much easier for them to figure out again. Password selection should not be taken lightly. Protecting yourself and your information is a high priority. Many people in America fall victim to identity theft because they left their information unprotected. Don't be the next victim.
You can click on the link below to get more useful information and to check to see if your password is strong enough.
www.microsoft.com/security
The chart below, provided by Microsoft, which I can use because I purchased the license key and was given rights to use Microsoft information by following the guidelines below, will give you an overview of what I taught you above:
Sources:
http://www.microsoft.com/- Microsoft allows usage if it is used for a school project if I follow the guidelines. This means no obscene or pornographic texts and I can't be defamatory towards Microsoft. I must also provide a link to Microsoft which I did above.
Strong passwords are usually 6-16 characters long. You will want to have at least one capital letter, one numeric value and one symbol in the password. The longer the password , the longer it will take for someone to figure out. An example of this would be: Jerremy93$. This could be your first name, the year you were born and any symbol that you might want to use. This ten digit code could take a person millions of years to discover. This is due to several different combinations that could be used even if someone knew my name and date of birth.
When you visit a website and set up an account, the server will ask you for personal information in case you forget your password. An example most commonly used is mother's maiden name. Since the input is case sensitive, you might want to be creative when entering the information. An example might be: hoLLoway. If a person knew my mother's maiden name, they would still have a hard time figuring out how it was entered.
Once you have created a password, the next step will be to change it frequently. This might be every six months or so. When changing your password, do not make the mistake of just changing one value such as Jerremy94$. If someone knows your password already, this would make it much easier for them to figure out again. Password selection should not be taken lightly. Protecting yourself and your information is a high priority. Many people in America fall victim to identity theft because they left their information unprotected. Don't be the next victim.
You can click on the link below to get more useful information and to check to see if your password is strong enough.
www.microsoft.com/security
The chart below, provided by Microsoft, which I can use because I purchased the license key and was given rights to use Microsoft information by following the guidelines below, will give you an overview of what I taught you above:
What to do | Suggestion | Example |
Start with a sentence or two (about 10 words total). | Think of something meaningful to you. | Long and complex passwords are safest. |
Turn your sentences into a row of letters. | Use the first letter of each word. | lacpasikms (10 characters) |
Add complexity. | Make only the letters in the first half of the alphabet uppercase. | lACpAsIKMs (10 characters) |
Add length with numbers. | Put two numbers that are meaningful to you between the two sentences. | lACpAs56IKMs (12 characters) |
Add length with punctuation. | Put a punctuation mark at the beginning. | ?lACpAs56IKMs (13 characters) |
Add length with symbols. | Put a symbol at the end. | ?lACpAs56IKMs" (14 characters) |
Sources:
http://www.microsoft.com/- Microsoft allows usage if it is used for a school project if I follow the guidelines. This means no obscene or pornographic texts and I can't be defamatory towards Microsoft. I must also provide a link to Microsoft which I did above.
Sunday, March 6, 2011
Presentation Project
Link: www.slideboom.com/presentations/315770/Donate-to-the-Muscular-Dytrophy-Association
As hard as it may be to conduct a self- critique, I think I can find a few things that I did well or could have improved on. As usual, I will start with what I could have done better. I did not ask questions in my presentation. I found myself often wondering how to put that in the presentation. I was asking for donations to MDA so I gave out more information and did not spark enough interest by asking questions. Reflecting on it now, I could have stated a sentence in a question form and then answered it in my presentation.
Since I failed on asking the questions, I most certainly did not answer them in the right place. I did however try to avoid any questions being presented from the viewer. I tried to make sure the presentation had enough information in it to avoid the viewer from wanting to ask questions in the middle of my presentation.
Lastly, I did not validate claims until the end. I viewed several presentations where the presenter stated where they got the information from and then went on to explain. I thought this was something I could of done in the course of my presentation. I did acknowledge my sources at the end, but a better way would have been to incorporate them into the presentation.
One of my greatest learnings was how to place audio into the powerpoint. I honestly did not realize how easy that could be. All that I had to do was click on slide show and then record narration. Timing the video to match the narration was a bit tricky, but well worth it. Having narration in a presentation for business will let the viewer hear how knowledgeable your are about a topic. I believe this also helps the viewer and the presenter connect even when they are miles apart.
As hard as it may be to conduct a self- critique, I think I can find a few things that I did well or could have improved on. As usual, I will start with what I could have done better. I did not ask questions in my presentation. I found myself often wondering how to put that in the presentation. I was asking for donations to MDA so I gave out more information and did not spark enough interest by asking questions. Reflecting on it now, I could have stated a sentence in a question form and then answered it in my presentation.
Since I failed on asking the questions, I most certainly did not answer them in the right place. I did however try to avoid any questions being presented from the viewer. I tried to make sure the presentation had enough information in it to avoid the viewer from wanting to ask questions in the middle of my presentation.
Lastly, I did not validate claims until the end. I viewed several presentations where the presenter stated where they got the information from and then went on to explain. I thought this was something I could of done in the course of my presentation. I did acknowledge my sources at the end, but a better way would have been to incorporate them into the presentation.
One of my greatest learnings was how to place audio into the powerpoint. I honestly did not realize how easy that could be. All that I had to do was click on slide show and then record narration. Timing the video to match the narration was a bit tricky, but well worth it. Having narration in a presentation for business will let the viewer hear how knowledgeable your are about a topic. I believe this also helps the viewer and the presenter connect even when they are miles apart.
Saturday, February 19, 2011
Tutorial 2: Creating an Excel Spreadsheet
Let's suppose that you are the manager of a local pizza chain and want to create an excel spreadsheet that will tell your employees how many pizzas to make ahead of time based on your forecasted sales. This will not only help you deliver the pizzas faster, but will eliminate waste as well. I will provide you with this step by step tutorial on how to do this.
- First, we want to create the outline of what it is we are tracking. Once you have opened your excel spreadsheet, take your cursor and click on the number 1 on the sheet. Doing this will highlight the entire row. Numbers are called rows and the letters are called columns.
- Once row 1 is highlighted, click on your "Home" tab. Under the home tab, you will find the word alignment. Click on the arrow to the bottom right of this word and another window will appear . In this window, mark the box "merge cells" and click OK. See screen shot below:
- Now name your spreadsheet "Pizza Prep Planning" into row one. Once you have named the spreadsheet click on "B" to bold it and then center it by pressing the button "center" above alignment.
- Take your cursor and click on cell 2A and type in "Day of Week". Name 3A "Forecasted Sales", 4A "Supreme", 5A "Meat Lover" and 6A "Pepperoni."
- In cell B2, place a "M" for Monday. Continue the day of the week process all the way through columns C-H.
- To clean our spreadsheet up, click between column A and B. This will widen the columns so that all the words fit. Continue this through to G-H.
- Now we want to add a border around our text. Click in cell A2 and while holding the left mouse button down, drag it over to column H and down through row 6. This will highlight the desired area.
- Under the home tab, in the font section, click the drop down arrow next to the black box outline. This is your borders section. Once you click the arrow, choose "all borders." Repeat this process, but this time click "thick box border." Now your area looks neat and professional.
Your spreadsheet should look like this so far:
Now we will move on to the mathematical formulas that we need to apply to this spreadsheet so it can do the math for us.
- First, plug into the spreadsheet what you have forecasted in sales for each day of the week. For this exercise, put ( starting Monday) 1500, Tuesday 1750, Wednesday 1900, Thursday 1950, Friday 3400, Saturday 4200 and Sunday 2500. In cell A8 write "supreme", A9 write "meat lover" and in cell A10 write "pepperoni." In cells B8, B9 and B10, plug in how many pizzas you will sell of each type in percentages. For this exercise, plug in 25% for supreme, 20% for meat lover and 37% for pepperoni. You can change this from week to week after the spreadsheet is finished. See below:
- Once you have finished plugging your sales in, click on cell B4. We will place this formula in: =($B8*B3)/12. All formulas MUST start with an = sign. We want to start with a parenthesis to separate the multiplication from the division. The $ sign will allow us to make the B8 cell absolute and not change when we copy the formula. The 12 is the cost of each pizza.
- Right click on cell B4 and choose copy. Hold down the mouse key and drag over to cell H4. Right click again and choose paste. This will copy that same formula all the way across the row.
- Since we can't make .25 of a pizza, we want our numbers to be whole numbers "without decimals." To do this, click on "decrease decimal" button right above the word "number" on your home tab. See below:
 |
- In cell B5 put in the formula =($B9*B3)/12 and repeat the copy and paste and decrease decimal.
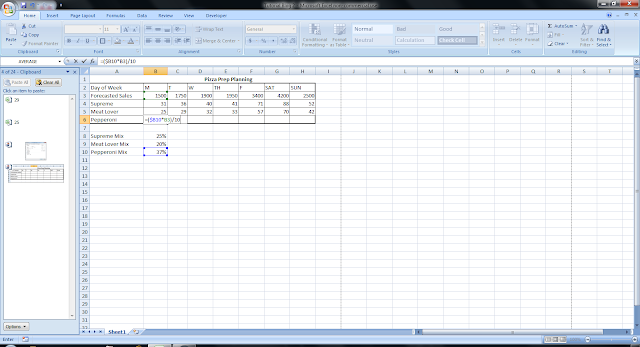
- In cell B6 place the formula =($B10*B3)/10. We will place a 10 in this formula because pepperoni pizzas are $2 cheaper than all others. Repeat decrease decimal and copy and paste. Below is an example of the formula:
Now that your spreadsheet is complete, you can change your forecasted sales or your mix percentage at any time. Since the formulas are already in place, it will change how many pizzas you need to make automatically. Your completed spreadsheet should look like this:
Sunday, February 13, 2011
Creating My Avatar
I must admit that this is the first time that I have ever created an Avatar. When our ISM class first started I went to Doppelme and Meez to try and create my Avatar and didn't care much for the process. This time I used TizMe and found the process much easier. You could spend hours dressing up your Avatar. My Avatar is a little more girly than I am in person. I say this because I would not go out with a cut off shirt and hip hugging pants. Just not my style. One thing I do like about mu Avatar is that I lost weight overnight!
Subscribe to:
Posts (Atom)